Are you confident your risk assessment coverage is truly comprehensive?
You’ve diligently mapped out potential threats, analyzed vulnerabilities, and implemented safeguards. Yet, lurking in the shadows could be hidden risks, silently threatening your organization’s stability.
Don’t let complacency become your downfall.
This isn’t about adding more stress; it’s about gaining clarity.
We’ll unveil 7 often-overlooked risks that might be slipping through the cracks of your current assessment. Discover blind spots, uncover potential vulnerabilities, and empower yourself to build a truly robust risk management strategy.
Take control of your organization’s future. Dive in and explore the hidden risks you need to know about.
7 Hidden Risks Your Risk Assessment Coverage Might Be Missing
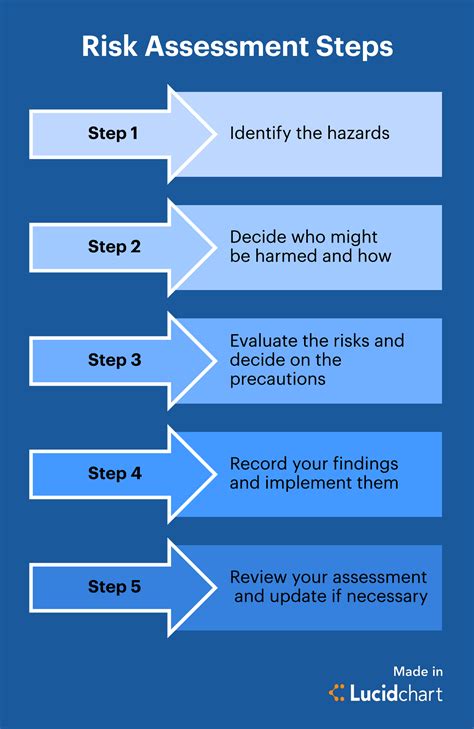
You’ve diligently conducted your risk assessment, meticulously identifying potential threats and vulnerabilities. You’ve mapped out mitigation strategies and feel confident in your organization’s preparedness. But hold on! Even the most thorough risk assessments can overlook crucial hidden risks lurking beneath the surface.
Failing to identify these hidden risks can leave your organization vulnerable to unexpected disruptions, financial losses, and reputational damage. Let’s delve into seven common blind spots that your risk assessment coverage might be missing:
1. The Rise of Emerging Technologies

The technological landscape is constantly evolving, with new technologies emerging at a dizzying pace. Your risk assessment might be outdated before it’s even finalized.
-
The Risk: Emerging technologies like artificial intelligence, blockchain, and the Internet of Things (IoT) introduce novel risks. AI algorithms can be biased, blockchain vulnerabilities can be exploited, and IoT devices can become gateways for cyberattacks.
-
Mitigation:
- Regularly review your risk assessment framework to incorporate emerging technologies and their associated risks.
- Stay informed about the latest technological advancements and potential vulnerabilities.
- Conduct specialized assessments for new technologies implemented within your organization.
2. The Human Factor: Insider Threats and Social Engineering

Humans are the weakest link in any security chain.
-
The Risk: Insider threats, whether intentional or unintentional, can cause significant damage. Employees with malicious intent can steal data, sabotage systems, or leak confidential information. Social engineering attacks, like phishing scams, can trick employees into divulging sensitive data.
-
Mitigation:
- Implement robust employee training programs on cybersecurity awareness, including social engineering tactics.
- Conduct background checks and implement access controls based on the principle of least privilege.
- Monitor employee activity for suspicious behavior and implement data loss prevention (DLP) solutions.
3. Third-Party Risk: Beyond Vendor Management

Your reliance on third-party vendors and suppliers exposes you to a wider range of risks.
-
The Risk: A vendor’s data breach, operational failures, or even unethical practices can directly impact your organization.
-
Mitigation:
- Conduct thorough due diligence on all third-party vendors, including security assessments and audits.
- Establish clear contractual agreements outlining security requirements and responsibilities.
- Monitor vendor performance and conduct periodic reviews to ensure ongoing compliance.
4. Supply Chain Disruptions: Beyond Natural Disasters

Supply chain disruptions can stem from various sources, not just natural disasters.
-
The Risk: Geopolitical instability, pandemics, labor strikes, or cyberattacks can disrupt your supply chain, leading to delays, shortages, and financial losses.
-
Mitigation:
- Diversify your supply chain to reduce reliance on single suppliers.
- Develop contingency plans for potential disruptions, including alternative sourcing options.
- Monitor global events and trends that could impact your supply chain.
5. Regulatory and Compliance Changes: Staying Ahead of the Curve

Regulations and compliance requirements are constantly evolving.
-
The Risk: Failure to comply with new regulations can result in hefty fines, legal action, and reputational damage.
-
Mitigation:
- Stay informed about changes in relevant regulations and industry standards.
- Implement a compliance management system to track changes and ensure adherence.
- Seek expert advice to navigate complex regulatory landscapes.
6. Data Privacy: Beyond GDPR

Data privacy concerns extend beyond Europe’s General Data Protection Regulation (GDPR).
-
The Risk: Data breaches, misuse, or unauthorized access to sensitive personal information can lead to legal liabilities, financial losses, and erosion of customer trust.
-
Mitigation:
- Implement strong data encryption, access controls, and anonymization techniques.
- Develop a comprehensive data privacy policy and ensure employee awareness.
- Conduct regular audits to assess data security practices.
7. Reputation Management: The Silent Killer

A single negative event can severely damage your organization’s reputation, impacting customer loyalty, brand value, and future growth.
-
The Risk: Cyberattacks, product recalls, or unethical practices can quickly spread online, leading to negative publicity and loss of trust.
-
Mitigation:
- Develop a proactive reputation management strategy, including crisis communication plans.
- Monitor online mentions and engage with customers to address concerns.
- Foster a culture of transparency and accountability.
Don’t Let Hidden Risks Catch You Off Guard

Conducting a thorough risk assessment is crucial, but it’s not a one-time exercise. Regularly revisit your assessment, adapt to changing circumstances, and stay vigilant about emerging threats.
By proactively addressing these hidden risks, you can strengthen your organization’s resilience, protect your assets, and safeguard your future.
FAQ
-
Q: What exactly is risk assessment coverage? A: Risk assessment coverage refers to the insurance policies and safeguards designed to protect businesses from financial losses arising from identified risks.
-
Q: Why is it important to have risk assessment coverage? A: Risk assessment coverage helps businesses mitigate potential financial losses, protect their assets, and ensure business continuity in the face of unforeseen events.
-
Q: Are there common types of risks that risk assessment coverage typically addresses? A: Yes, common risks covered include property damage, liability claims, cyberattacks, natural disasters, employee injuries, regulatory fines, and operational disruptions.
-
Q: What are some examples of hidden risks that might be missing from standard risk assessment coverage? A: Examples include emerging technologies risks, supply chain disruptions, reputational damage from social media, climate change impacts, intellectual property theft, data privacy breaches, and pandemic-related losses.
-
Q: How can businesses identify hidden risks that their coverage might be missing? A: Businesses can conduct thorough risk assessments, consult with insurance brokers, stay informed about industry trends, monitor emerging threats, and regularly review their coverage policies.
-
Q: What steps can businesses take to address hidden risks? A: Businesses can implement risk mitigation strategies, purchase additional insurance coverage, invest in cybersecurity measures, diversify supply chains, establish crisis management plans, and foster a culture of risk awareness.
-
Q: Where can businesses find resources to learn more about risk assessment coverage and hidden risks? A: Resources include insurance industry associations, professional risk management organizations, government agencies, industry publications, and online research platforms.




